As terms such as "data breaches," "vulnerabilities," and "cyber attacks" continue to appear more frequently in the news, it's crucial to remain alert and bolster cybersecurity measures. This article offers insight into Canary Tokens, a user-friendly and efficient tool designed to protect personal data. It elaborates on how Canary Tokens can be utilized to set traps and track possible espionage attempts.
Canary Tokens: A smart shield that instantly alerts you to any unauthorized intrusion into the world of digital security
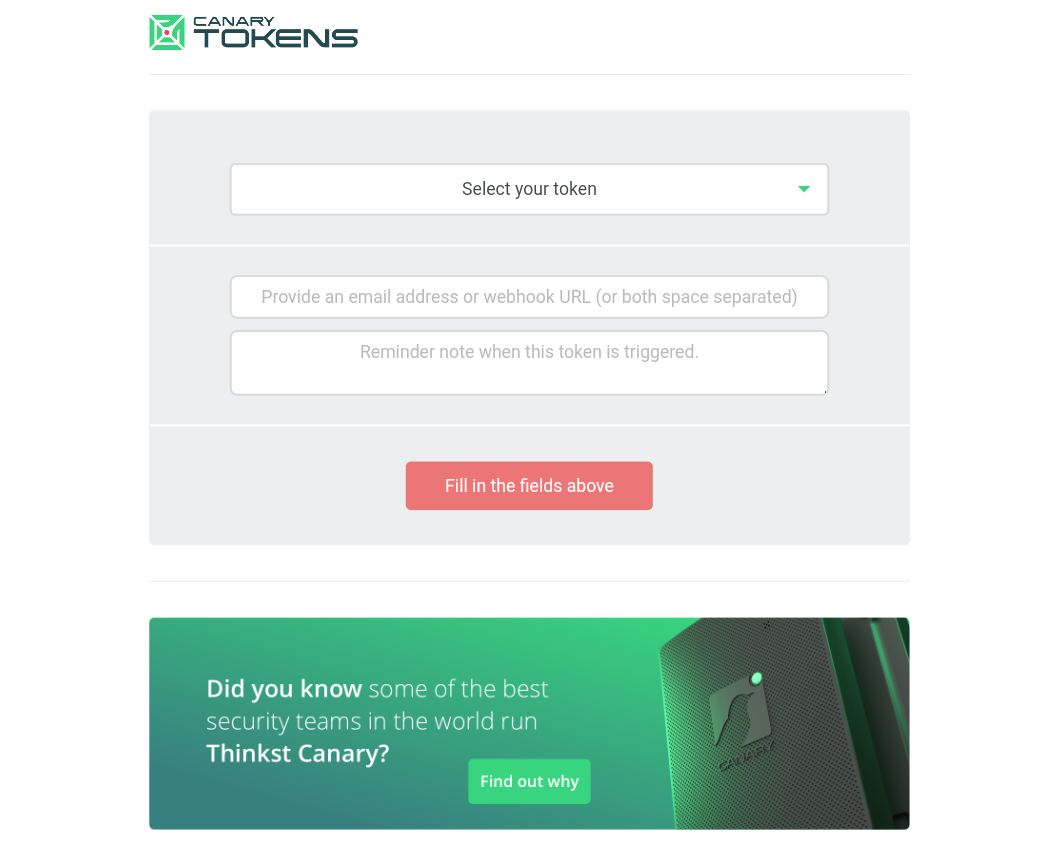
Canary Tokens acts as an early warning system for suspected unauthorized access to personal data, by placing a file planted with a hidden link that activates when opened by a hacker. Head to the Canary Tokens website to create your first token, where you'll find illustrations of the creation procedure.
How to use Canary Tokens to create traps and monitor potential spy activities
Canary Tokens offer a variety of distinctive tokens that can be used for tracking and detecting electronic intrusions. This includes Microsoft Word files, PDF files, Windows folders, URL links, and even API keys, allowing users to choose the most suitable type for their needs.
- Enter the Canary Tokens link and then create and copy codes, to ensure you receive notifications in case the token is activated, you must enter a valid email address during the code setup.
Upon activation of the token, the accompanying note serves to clarify its purpose and category, facilitating easy recognition upon notification receipt. For instance, including a note like "Unique token for personal document folder" helps specify its nature.
Upon completing these steps, selecting "Create Canary Token" generates the token, after which the resulting file can be downloaded and strategically stored on the device to aid in monitoring and identifying electronic breaches.
What is Canary Token?
To ensure personal protection and maintain information confidentiality, an innovative strategy can be followed to lure intruders and hackers. This can be achieved by renaming the file to something enticing for hackers, such as "Confidential Information" or "Passwords." This file should be placed in a specific folder, such as the Documents folder or the desktop, where the intruder or hacker might expect to find it.
Next, the file is programmed to send a notification or email to the user's email address when opened. This allows the user to know if anyone is attempting unauthorized access to their devices. Consequently, the user can take necessary actions to protect their information and device from unwanted intrusion and seizure.
This strategy relies on the concept of using artificial intelligence to execute the desired action when the file is opened, making it an effective means of quickly and efficiently verifying intrusion attempts and infiltration.

.jpeg)
.jpeg)