Keylogger tools are a serious security threat to Windows-based computer systems. Their objective is to monitor keystrokes and detect sensitive data for infiltrators and surveillance agents. Therefore, it is important to detect these threats in advance before they can cause any significant harm. Join us to learn about some of the best ways to detect keylogging software on a Windows-based computer.
How to detect keyboard spy tool in Windows systems
A Keylogger is a software or hardware tool that monitors the keystrokes entered on a computer/laptop or mobile device's keyboard. Keylogging software can be introduced using USB devices or deceptive driver programs, but they are relatively easy to detect and remove. However, Keylogger software can be more stealthy and may not be easily detectable.
Why are Keyloggers considered dangerous?
Keyloggers can be dangerous because they can capture sensitive information such as passwords, credit card numbers, and other personal information without the user's knowledge. This information can then be transmitted to a remote attacker who can use it for malicious purposes such as identity theft or financial fraud.In the wrong hands, Keyloggers can be a powerful tool for cybercriminals to gain access to confidential information. Therefore, it is important to take appropriate measures to protect your device from Keyloggers, such as using anti-virus software, avoiding suspicious links or attachments, and being cautious about sharing personal information online.
Unlike viruses and regular Trojans, remote keyloggers do not affect system performance but cause a lot of damage by exposing your private information to others, think financial information, credit card data, PINs, passwords, anonymous posts and comments online.
How to detect and remove Keyloggers
If you suspect that your Windows system has been attacked by a keyboard logger Keylogger, follow these useful steps to detect and/or remove keyboard logging software.
Using Task Manager
Open the Task Manager with a simple right-click on the taskbar.
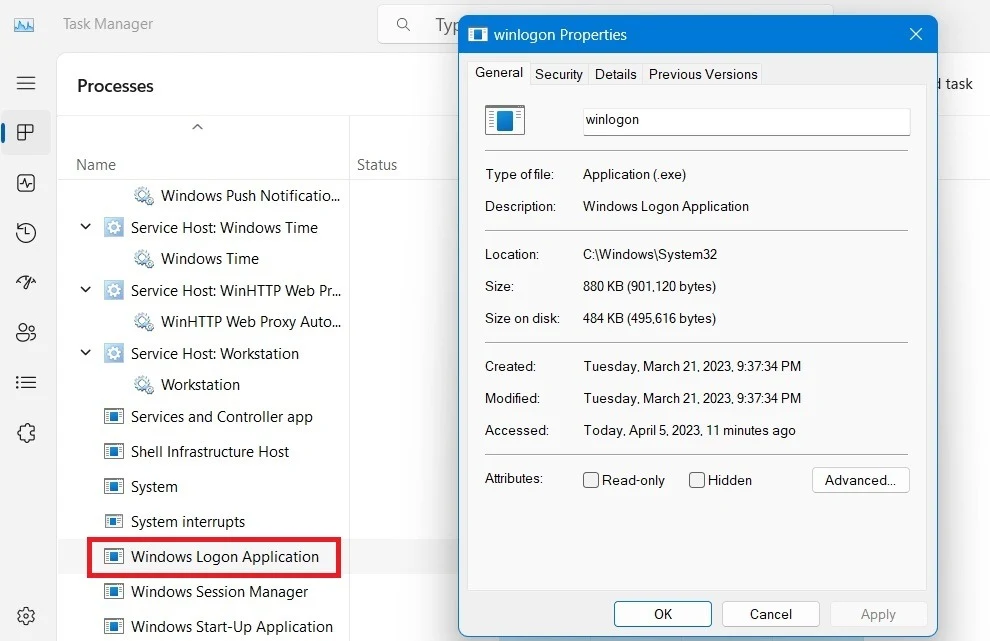
»Moved to background processes and switched to the Windows Logon application.
»If it contains a repeated input - unusual if you are the only person using the computer - such as "Windows Logon (1)", this means that someone else has logged into your Windows system.
»This is the first sign of a possible keylogger, then right-click and quit the program.
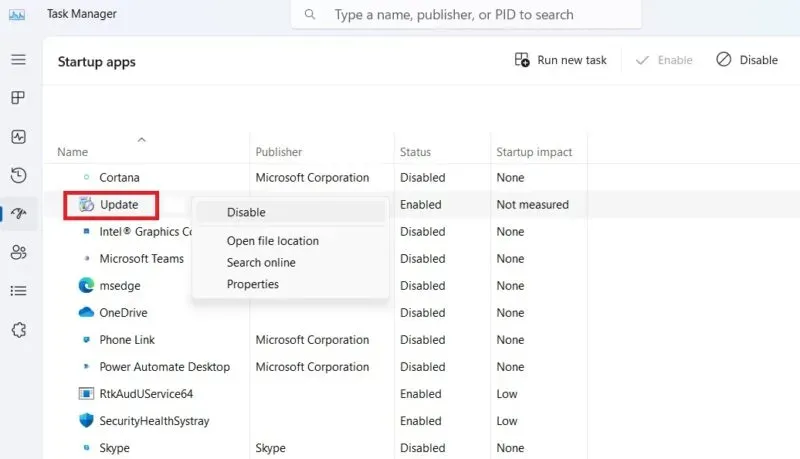
»Also, check the "Startup" tab where you don't need most of these programs during startup, so disable them, which reduces the likelihood of a keylogger program entering during Windows startup.
»The only programs that belong to the startup list are audio codecs like Realtek (which without it there will be no sound), the browser you're using most likely, and the SecurityHealthSystray.exe program. Everything else is optional.